Safety Discovers ReDoS Vulnerabilities in Top Python Packages (Part 2)

Safety’s Research to Discover Novel Vulnerabilities
As the maintainer of the industry-leading database of Python vulnerabilities and malicious packages, Safety conducts extensive research to identify novel vulnerabilities. As a result of this research, we offer protection from - and insights into - more than 14,000 Python vulnerabilities.
One of the ways we achieve this breadth of coverage is by examining the most frequently-downloaded Python packages. In the past month we analyzed every Python package with more than 20 million downloads, and made several discoveries of note.
Pygments
Pygments is a syntax highlighting package written in Python designed to convert source code into formatted text with appropriate colors and styles for easier readability. Pygments is downloaded more than 45 million times each month, meaning any vulnerability could have wide-reaching consequences.
Vulnerability Details
The regular expressions used when parsing Smithy, SQL/SQL+Jinja, and Java properties files were discovered to be vulnerable. As a result, pygmentizing a maliciously-crafted file of these kinds would have resulted in high resources consumption or crashing of the application.

Impacted Versions
Pygment versions <2.15.0 are impacted by this vulnerability when parsing Smithy, SQL/SQL+Jinja and Java properties files from untrusted sources.
Patches & Vendor Response
It is stated clearly in the repository that “Pygments provides no guarantees on execution time, which needs to be taken into consideration when using Pygments to process arbitrary user inputs.”.
However, after our disclosure, the maintainers acknowledged the issue, and then applied fixes between the releases 2.14.0 (for Smithy lexer) and 2.15.0 (for Java properties and SQL+Jinja lexers).
Assigned Identifiers
Safety Cybersecurity ID: 58910
CVE: CVE-2022-40896
AWS Command Line Interface (awscli)
The AWS Command Line Interface (CLI) is a unified tool developed by Amazon Web Services to manage AWS services from the command line. As one of the most popular packages, awscli is downloaded more than 230 million times each month.
AWS CLI provides a consistent interface for controlling multiple AWS services, allowing developers and administrators to automate and script their AWS infrastructure management tasks.
Vulnerability Details
The _SOURCE_REGEX regular expressions in the NuGetBaseLogin class was identified as being vulnerable. As a result, NuGetLogin and DotNetLogin classes were also affected by the vulnerability.
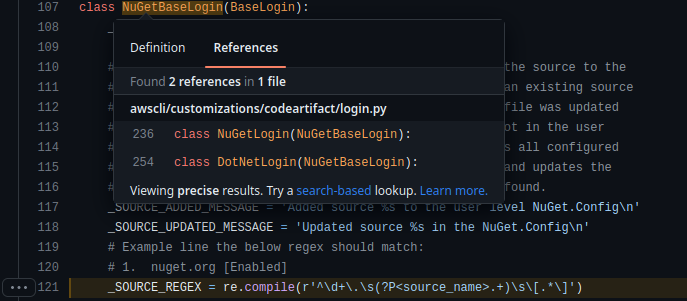
Impacted Versions
Awscli versions <1.27.90 are impacted. However, an attacker would need local access or be able to provide a malicious nuget.config file in order to exploit the vulnerability.
Patches & Vendor Response
Considering that special conditions are needed for an attack to succeed plus the limited scope of impact in preventing authorized users from logging into CodeArtifact's provider, this issue was not considered security relevant by AWS. It was, however, fixed in awscli version 1.27.90.
Assigned Identifiers
Safety Cybersecurity ID: 58911
Vulnerability Scanning with Safety CLI
These vulnerabilities underscore the critical importance of robust security measures when leveraging open-source Python dependencies. With new vulnerabilities being discovered in even the most popular of packages, it is important to monitor and scan development environments and production systems on a continual basis for the presence of newly-identified vulnerabilities.
To learn more about how Safety’s industry-leading vulnerability research and software supply chain security products, please contact us or reach out to info@safetycli.com.
We extend our gratitude to Sebastian Chnelik, our Cybersecurity Analyst, for his invaluable research and discovery.
Reduce vulnerability noise by 90%.
Get a demo today to learn more.



.png)